

Phil Emer, director of Technology Planning and Policy at the Friday Institute for Educational Innovation, gave lawmakers a sobering look at the cybersecurity landscape during Tuesday’s Joint Legislative Education Oversight Committee meeting.
He briefed lawmakers on the state’s efforts to combat cybersecurity threats. He also offered information on how districts and schools can do to better protect themselves in the wake of a 2016 Department of Public Instruction study showing most traditional public and charter schools are not ready for a significant cybersecurity event.
“Schools are actually getting targeted specifically now,” he said. “Not only have North Carolina schools been targeted, but a lot of municipalities and counties in the state have been targeted.”

One of the more high-profile hacking attacks in the state came late last year when hackers froze Mecklenburg County’s government and demanded a ransom.
Emer noted one district suffered a similar ransomware attack and had to rebuild its digital infrastructure shortly before the start of the school year because it had no digital backups in place.
He also gave the example of three other districts that asked MCNC, the tech non-profit that operates the broadband infrastructure for the state’s schools, for help following malware attacks.
“A number of devices in a school district will be infected, they’ll clean them, and then almost immediately they become reinfected,” Emer said.
He said that practicing good “cyber hygiene” could prevent such attacks, which can end up being costly for districts.
The state now appropriates $200,000 each year for an initiative dealing with cybersecurity and risk management. Emer said at present the state is in the “continuous monitoring and risk assessment” phase of a three-step process of the initiative.
As part of that, a risk assessment dashboard has been created that can check for vulnerabilities, see what issues need attention, calculate risk scores, apply fixes, and more.
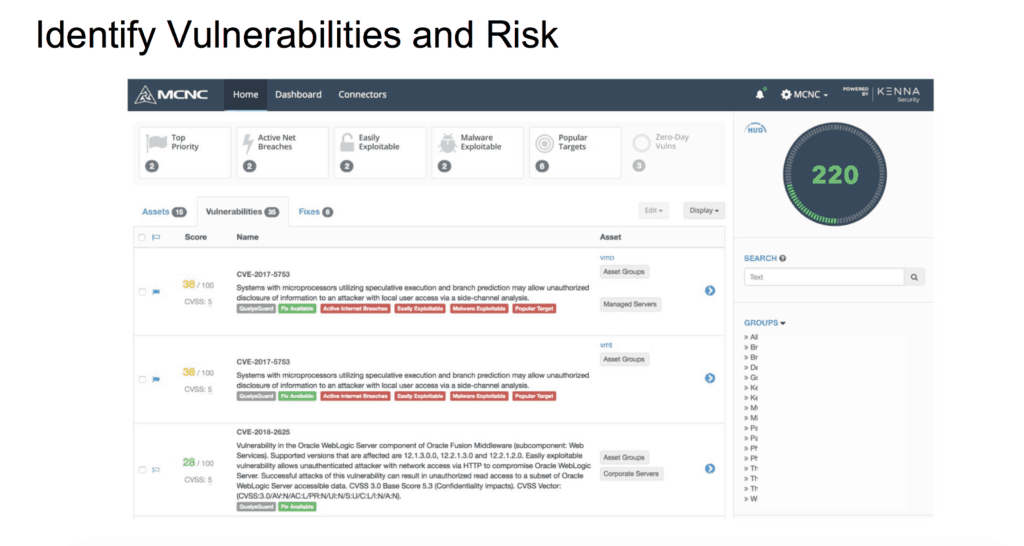

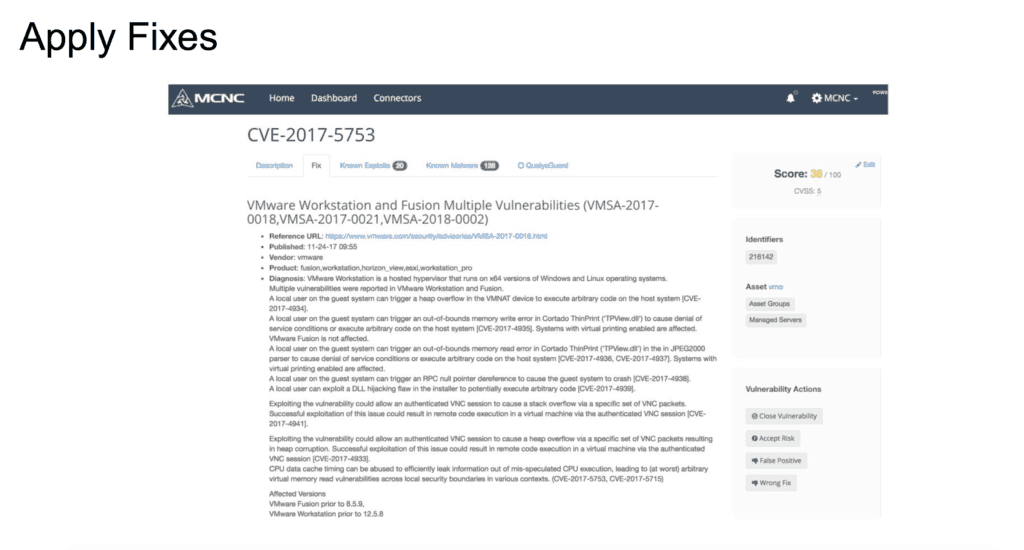

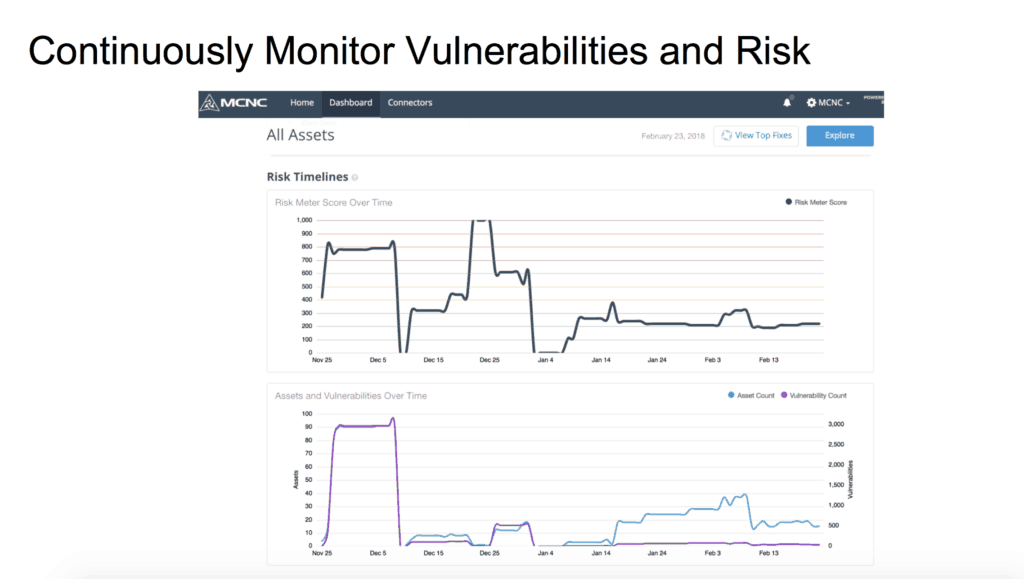

Three school districts are beta-testing the system with more being added in the next few weeks. The system will roll out to all schools and districts after testing is over in spring 2018.
Emer ran down a list of the different kinds of attacks used on school systems, but he said there is one particular strategy that ends up being most effective for hackers.
“Beyond all, the entire point for virtually all the risk and all the hacks tends to be e-mail,” he said, adding later, “It’s easy, it’s relatively simple to get someone to click on a link inside of an email, and it’s cheap. They don’t have to spend a whole lot of hacking time to do that.”
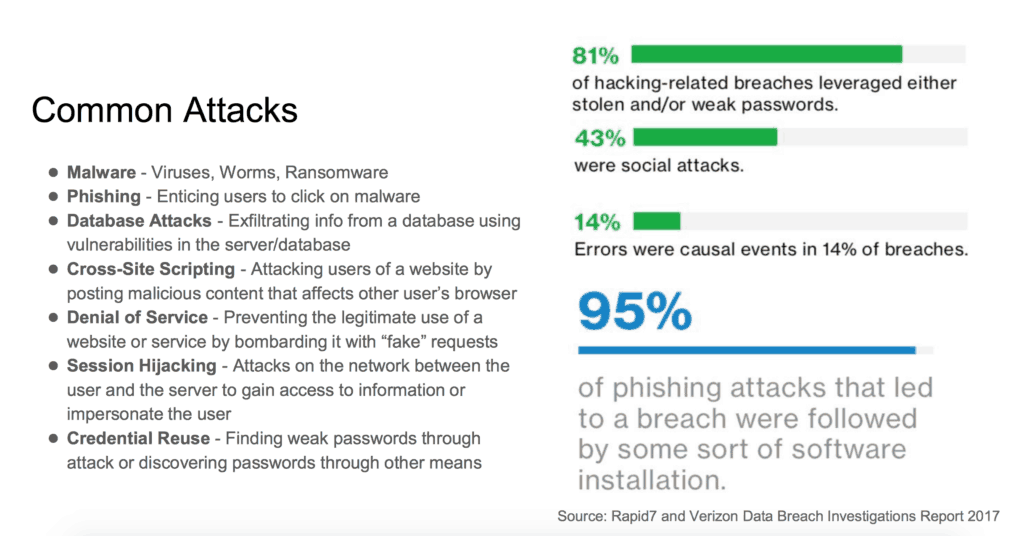

Recently, school district accountants and chief financial officers in the state have been getting e-mails from their superintendents asking for W-2s for employees in the schools, Emer said. The only catch is that the e-mails were not actually from the district superintendents.
“At least one school district fell for that one last year,” Emer said.
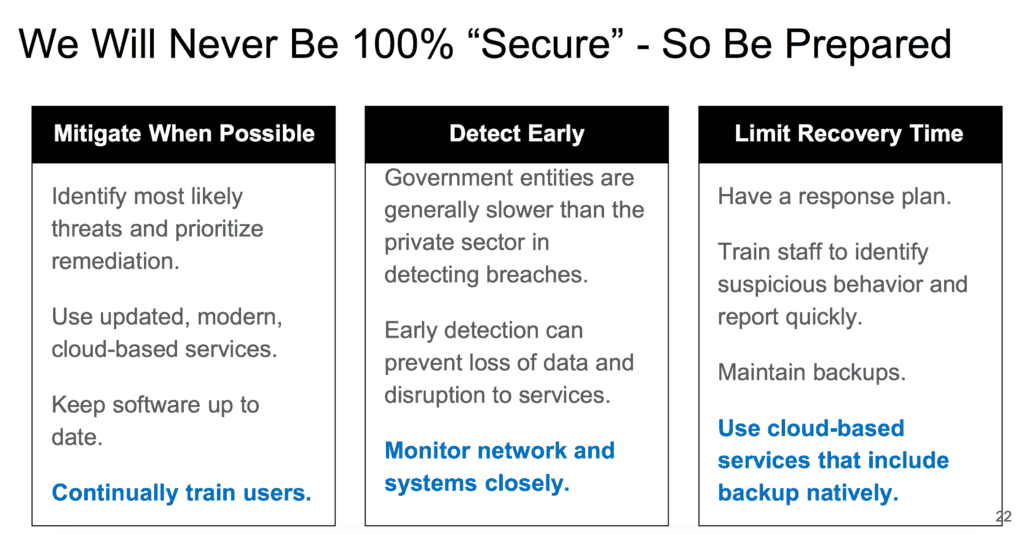
The state has not “been sitting idly by,” Emer said. MCNC has incorporated denial-of-service attack mitigation into their service and, as a result, that kind of attack is almost a non-issue now for state school districts, he said. He also said there are strategies districts across the state can use to lessen the chance of falling prey to such attacks. But he cautioned, there is no silver bullet.
“No matter how much money we spend or what we do, we will never be able to protect everybody 100 percent,” he said.

After the presentation, lawmakers weighed in.
“I’m not a tech expert. Not even a tech geek,” said Sen. Joyce Krawiec, R-Forsyth, before adding: “It’s fascinating the lengths that hackers will go to get into systems.”
Sen. Ronald Rabin, R-Harnett, worried that the ultimate responsibility for preventing cybersecurity threats did not really reside with anyone in particular.
“I’m surmising from what you said that this cybersecurity, there’s a serious threat in the K-12. I also heard you say that nobody is really responsible to maintain it,” he said to Emer, before asking him where the responsibility should be.
Emer said the state should be setting the targets but that local technology staff were going to be responsible for what happened in school districts. Rabin said that the buck needed to stop at one particular level.
“That responsibility has to be fixed, or it’s not a serious threat,” he said.
Students have been responsible for some hacking attacks in the state, but not many, Emer said. In some cases, he said students have initiated denial-of-service attacks on schools, and he even mentioned students going to websites and buying such attacks so they can then initiate them on test days. But Emer said that most hacking attacks are coming from professional syndicates.
Correction: The headline originally read “Tech experts cautions state schools unprepared for cybersecurity events.” It has been corrected


